Crosstech IEDD and C-IED Capability
The operational experience amongst the staff of Crosstech covers the whole gambit of military and humanitarian IEDD operations, specialised support to Special Forces, EOD search and response tasks, military and police exploitation and forensics and commercial and NGO de-mining. At a strategic level, senior management personnel within Crosstech’s Geneva HQ also provide a far reaching and in-depth capabilty and training resource.
Crosstech has a wealth of experienced instructors and staff in the field of EOD/IEDD, who have delivered high class training to hundreds of individuals Worldwide. Crosstech believes that quality of service and instruction is manifest in the experience and capability of their instructors and the support framework that the organisation provides. Crosstech follows an in depth and internationally respected systems approach to training method in all its consultancy, training design and delivery, which is further complimented by the professional delivery of Crosstech instructors and management staff. Key areas of IEDD and C-IED that Crosstech can provide are:
- Advanced IEDD Training. Advanced training covers IEDD operations and skills within varying threat environments from insurgent, non-permissive environments to specific support requirements for other security actors such as SWAT/specialist police teams and Special Forces. Other factors may include light scale IEDD operations where equipment use is limited/restricted or the environment/weather restricts operational capability. Crosstech staff have a strong track record of delivering this level of training both within national institutions and in an expeditionary role.

IEDD training, Morocco

Post Blast Forensic Exploitation Training, Afghanistan
- Post Blast Forensics and Exploitation. Traditionally titled, “weapons technical intelligence” (WIT/WTI), exploitation training can cover a number of disciplines and roles from the basic field operative to specialist forensic explosive teams and level two/three intelligence analysts working with formation headquarters of national laboratories. Exploitation has proven its worth within a number of conflicts Worldwide and is now a critical element of the combined operational/intel driven C-IED fight.
- IEDD operations are often coupled with other agencies, not least search assets; intermediate and advanced EOD search are critical disciplines which are utilised today for essential patrol lifesaving operations and clearance of vulnerable areas. There are also a number of advanced search team operations that compliment planned high threat IEDD operations. Crosstech has a plethora of experienced search instructors with many years of experience in training design and delivery.
- Command and Control (C2). The management structure of EOD/IEDD operations is critical, ensuring that correct capabilities and assets are in the correct environment on suitable response times is key to operational success. This C2 element to operations should also be integrated with threat analysis, threat/risk mitigation techniques, intelligence assets and all other agencies, such as fire service, police, medical and critical incident response units/HQs. Crosstech has staff who have operated at all levels of the EOD command structure from commanders on the ground to HQ staff and strategic oversight directors.

- Attack the Network (AtN). In today’s asymmetric conflict environment, counter-insurgency (COIN) operations and counter-IED operations go hand-in-hand. The integrated approach, from combining operations and intelligence, provides commanders and EOD operators a valuable support network of advanced and knowledgeable subject matter experts. Coordination of these key assets and training in analysis of critical information and C-IED data helps commanders and strategic staff within organisations to better manage threat. Such an integrated network of assets and specialist capability is critical in defeating/protecting against any insurgent or asymmetric threat. Crosstech has a strong history of delivering training on this bespoke intelligence/operational analysis tool to military and police commanders within NATO and specific country organisations.
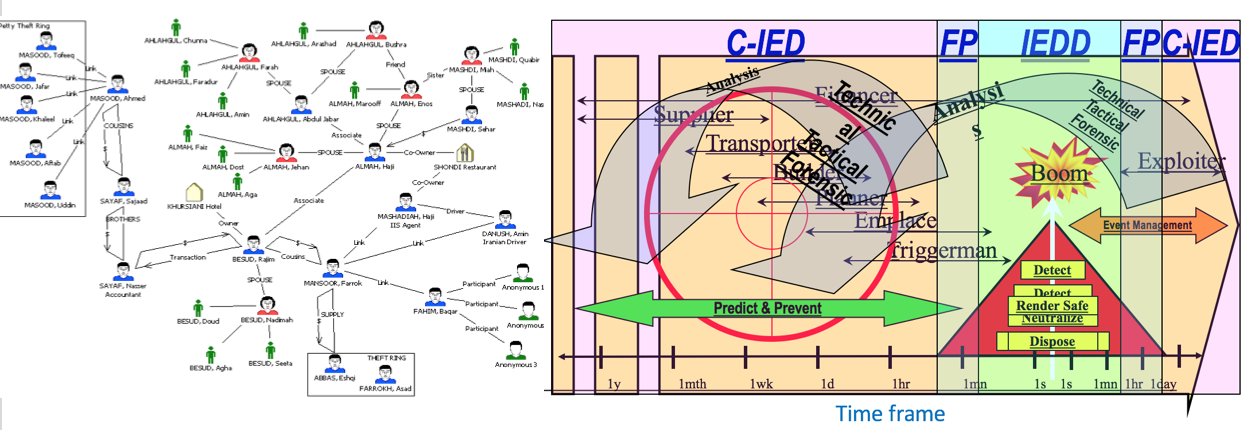
Attack the Network Philosophy, Analysis and C-IED Model Training
